ASaaS: The Pain We Address
The media continues to report large scale retailers being breached, exposing millions of customer credit cards, resulting in massive eight figure financial losses combined with priceless loss of customer trust in their brand identities. Financial institutions are hacked almost daily for monetary gain. Enterprises continue to spend hundreds of millions of dollars on IS/IT security. Why then, do so many high profile breach incidents continue to surface almost weekly in the media?
According to the Ponemon Institute, “71 percent of developers say application security was not adequately emphasized during the application development life cycle”.
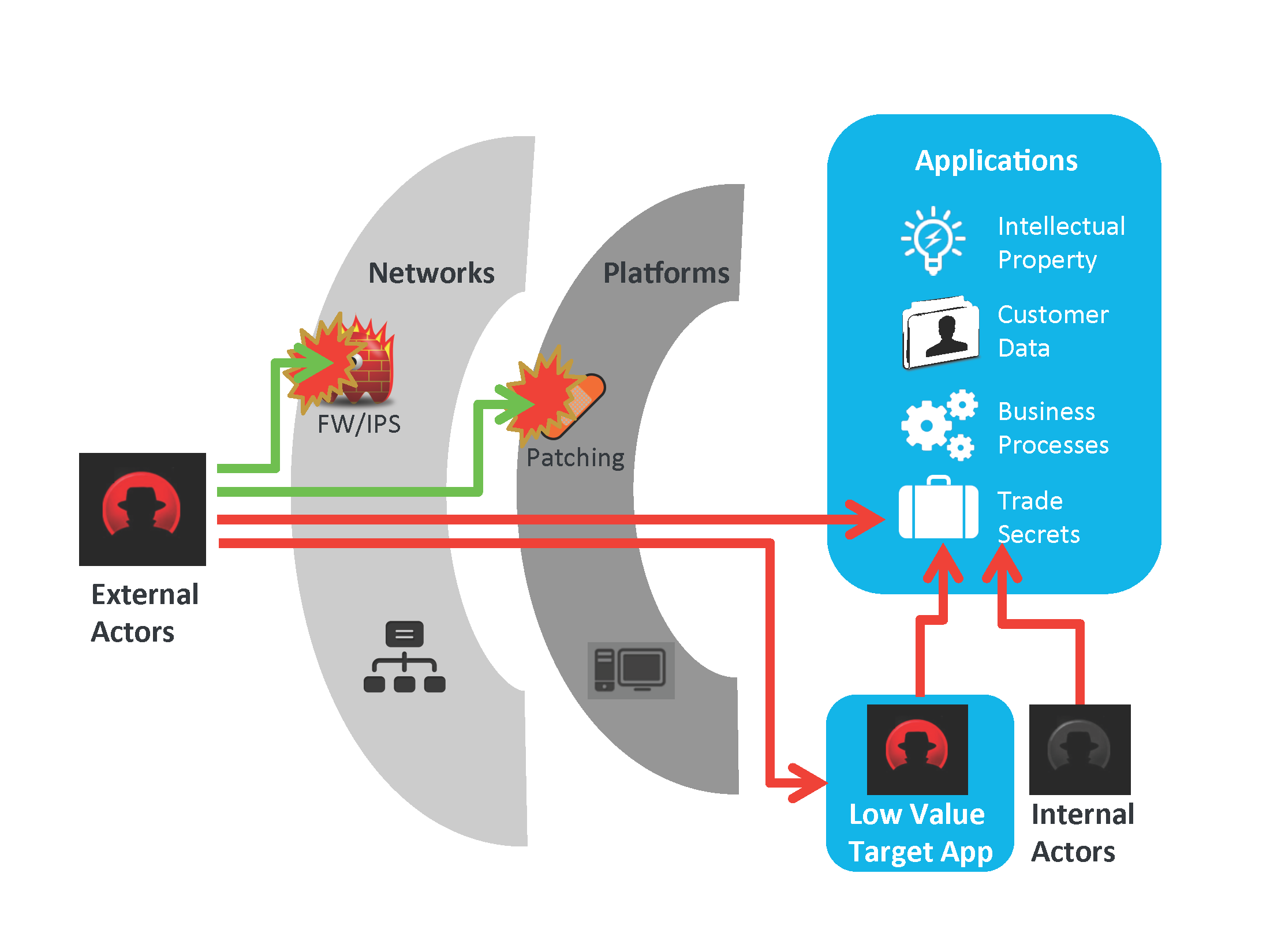
Highly motivated criminal actors know the networking infrastructure is heavily defended on the perimeter and simply is a means to an end, the real value target are the applications themselves, so why not target them directly? Experienced security teams know their perimeter defenses get breached regularly, and indeed this awareness should be the base assumption of all corporate information security strategy. The old world notion of safety within a secure perimeter simply no longer applies.
Applications themselves must now have both security built into code proactively and be specifically tested for security dynamically. This is the essence of our Application Security-as-a-Service.
ASaaS: The Solution We Provide
The 360Secure Application-as-a-Security offerings enable security to become embedded into the Software Development Life Cycle (SDLC) of a specific web application or non-web traditional application through one or more of the following methods;
- Security Quality Assurance Testing throughout the SDLC (otherwise known as DAST, or Dynamic Application Security Testing) for vulnerabilities throughout each release.
- Source Code Analysis (otherwise known as SAST, or Static Application Security Testing) for an even more proactive stance to remediate vulnerabilities at their source.
- Business Logic Analysis for deeper analysis of application security within your business context.
This service will reveal how appropriately the application maintains confidentiality, integrity and availability requirements through:
- Detection of common web infrastructure and application vulnerabilities.
- Analysis of transport layer, session management, and business logic attack vectors.
- Attempts to confirm detected vulnerabilities using restricted, non-invasive methods.
- Attempts to compromise the application, its host, and its environment.
- Subversion of application logic and/or pre-existing security controls.
- Attempts to gain elevated access and/or extract sensitive information.
ASaaS: The Benefits
Applications security is a specialized discipline requiring diverse skills across a range of programming and systems design, information security and business process flow knowledge bases. Simply running a scanning tool once involves a steep learning curve and declining benefits since an application scan can become immediately null and void upon the next release. Our Application Security-as-a-Service offering will have contextual memory of each release of the application life cycle. Our skilled security analysts don’t just regurgitate thousands of context-less security warnings. By utilizing our years of experience and advanced technologies we can filter and apply judgement to warning and symptomatic events and provide real, actionable information to deliver your applications. The following benefits that can be realized by Application Security-as-a-Service are summed up by these three main categories.
Skilled Application Security on Demand
- Target only a few applications to focus special skills where business critical
- Scale up to many applications in sophisticated environments on demand
- Enable instant support of multiple frameworks such as Java, .Net, PHP, C++ etc.
- Skilled analysts will semantic-filter false positives and voluminous “warning” events
- Free developers under tight time frames and constraints to focus on delivering applications
Security Enabled in the Software Life Cycle
- Prioritize security issues over multiple releases in decreasing levels of criticality and severity
- Trend toward zero security defects by criticality, versus inflexible security gating
- Leverage learned knowledge of the application and its business logic at each release cycle
Ongoing and Actionable Security Information
- Distinguish highly critical security defects with prioritization recommendations
- Detailed trend reporting for each iteration of the development cycle on an ongoing basis