Team Vision
At 360Secure, we fundamentally believe that IT security has gotten too complex, too reactive and has become too ineffective. IT Security needs a different approach. This approach is embodied by the following key quote from the independent and well-respected Ponemon Institute:
“Research has shown that the application layer is responsible for over 90% of all security vulnerabilities…”
“Yet more than 80% of IT security spending continues to be at the network and endpoint layer”
Clearly there is a mismatch between where the security issues are, and where the security budget has been going. We need to move from a reactive stance to a proactive stance addressing the applications themselves, at the source of the vulnerabilities. We need infrastructural IT security that is more cost-effective and more automated and therefore more reliable. Rather than an over-simplistic product / tool approach spewing context-less information, at 360Secure we believe that security must be provided as a knowledgeable and informed service with flexibility and customer context in mind to provide our customers real, actionable information.
Security-as-a-Service Becomes Business Enabler
The age of cloud computing, virtualization and mobile technology is upon us and a new era of rapid customer enhancing solutions has been ushered in by this technology. Groups become self-enabled through SaaS (Software-as-a-Service) to solve business problems independently of their own IT. Unfortunately, IT security issues have also exploded directly as a by-product of this technology progress. Rapid deployment of new customer enhancing IT capabilities is vital to the business to compete. How can we thus enable new business solutions quickly while appropriately dealing with the increased security risks?
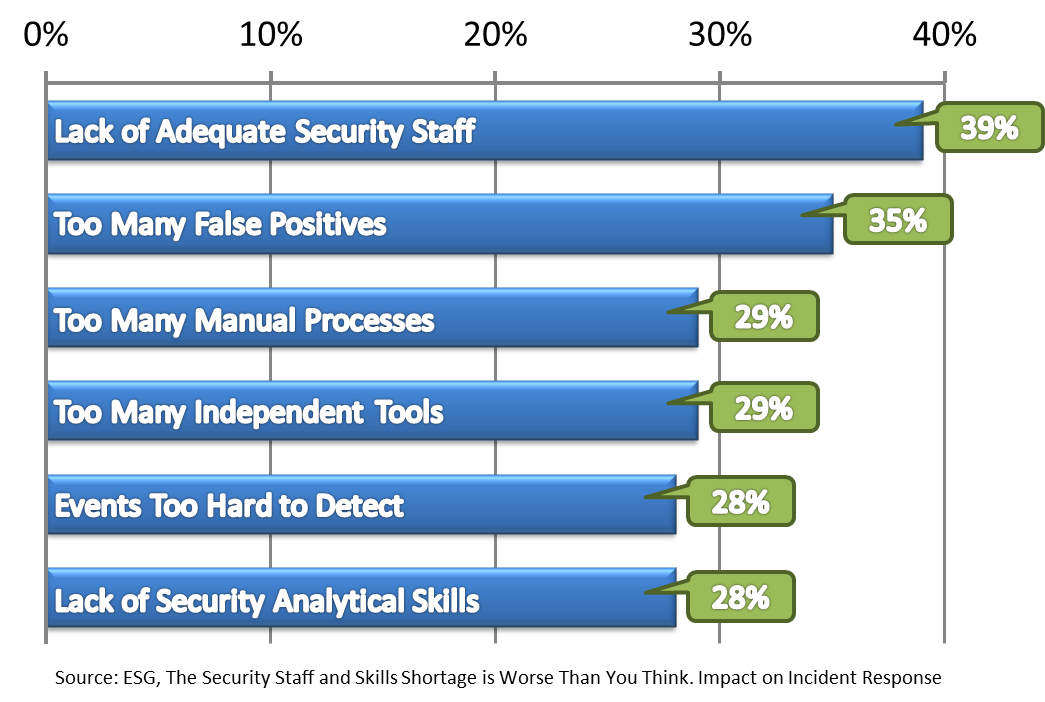
With the latest headline grabbing, high profile breaches against well-resourced corporate entities with large security organizations, clearly the status quo is not working. Based on research done by the ESG group, it would appear a fundamental foundation of the issue is a lack of available accredited security skills. What may come as no surprise is the fact that fully 83% of those surveyed say recruiting information security professionals is “difficult to extremely difficult”. Other issues impacting incident detection / response are cited below by ESG.
Additionally, with the stakes so high, every organization would benefit from an accredited partner that can apply security services on demand to assume some of the pressure and accountability as IT solutions ever expand. According to Gartner, as a means to obtain business velocity with security, it is becoming apparent that all IT application solutions and infrastructure will need to be validated by a credible and highly skilled third party.
“By 2015, more than 70% of enterprises will require proof of SAST testing from their
outsourcing, SaaS, cloud, and commercial software providers.” – Gartner
Security-as-a-Service Key Benefits
The following key benefits apply to all of the 360Secure Security-as-a-Service offerings;
- Gain a highly specialized, independent and credible partner to validate your security posture.
- Highly skilled, experienced and accredited security resourcing becomes immediately available “on demand” to your corporate entity for a fraction of the cost and recruitment difficulties.
- On-demand service offerings can systemize as much security as your organization needs, or can simply augment existing capabilities in weaker or more resource-constrained areas.
- Ongoing and actionable security information is the service delivery result, not a cryptic point product generated security report without any meaningful context to your business.